Recently I had reason to investigate a reported vulnerability in the YUI 2 library. CVE-2022-48197 claimed cross-site scripting in the TreeView component, but provided very little detail. Was this a real security issue?
Low-Quality CVE Report
The initial CVE-2022-48197 report had a vague description, very few references and seemed not to have been credited elsewhere on the Internet. This raised initial question marks.
- There really seem no references/ supporting info on the Internet to support the fact this CVE is significant.
- Snyk’s vulnerability listing for YUI includes reports linking to CVEs involving SWF and JSON parser, but does not include CVE-2022-48197.
- The Github repo supposedly documenting the vulnerability has a README.md file and claimed reproducer URLs.
- The “reproducers” are a range of localhost URLs which don’t work.
- The PHP files they reference (‘up.php’, ‘sam.php’ etc) aren’t in the disclosure repository, but appear to correspond to YUI sandbox/ samples in the YUI repository.
- Neither ‘up.php’ nor ‘sam.php’ are included in the YUI 2.8.2 Zip download from YUI 2 API Docs and Archives.
- The reporter has a LinkedIn profile which claims to have spoken at a middle-east cybersec conference and taught briefly at a university.
Overall the report seemed vague, nobody else on the Internet has accepted it as important, and the reproducers were sketchy. But there was enough to try it — so it shouldn’t necessarily be dismissed out of hand.
Reproducing the Issue
While the indicated PHP files (‘up.php’, ‘sam.php’ etc) are not in the distribution, they are in the ‘sandbox’ folder of the repository.
I tried to get the referenced examples working:
- I downloaded the YUI 2.8.2 repository (tag 2.8.2-8) and installed PHP.
- I ran PHP with its embedded webserver, serving from the root folder of the downloaded repository.
- I had to copy some CSS around & slightly adapt paths in the CSS to make the YUI TreeView examples viewable.
- Copy ‘tree.css’ from /sandbox/treeview/css/default to /sandbox/treeview/css/local
- Change image paths in the copied ‘tree.css’ from ../../../../../../../i/us/nt/widg/tree/dflt/ prefix to ../../img/default/.
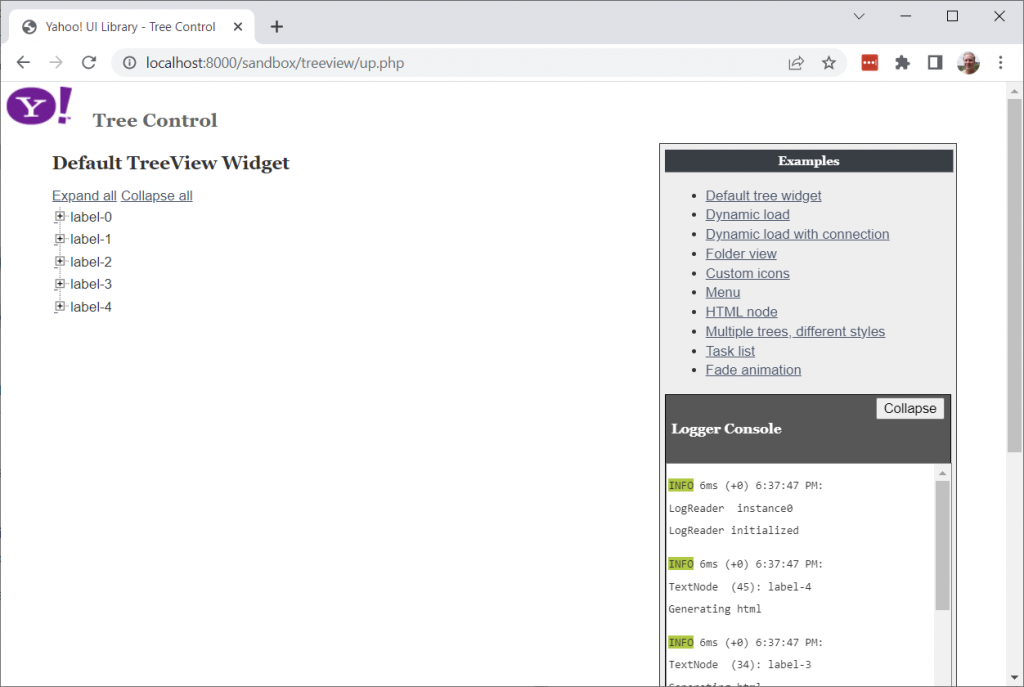
Success! I was able to see some TreeView examples.
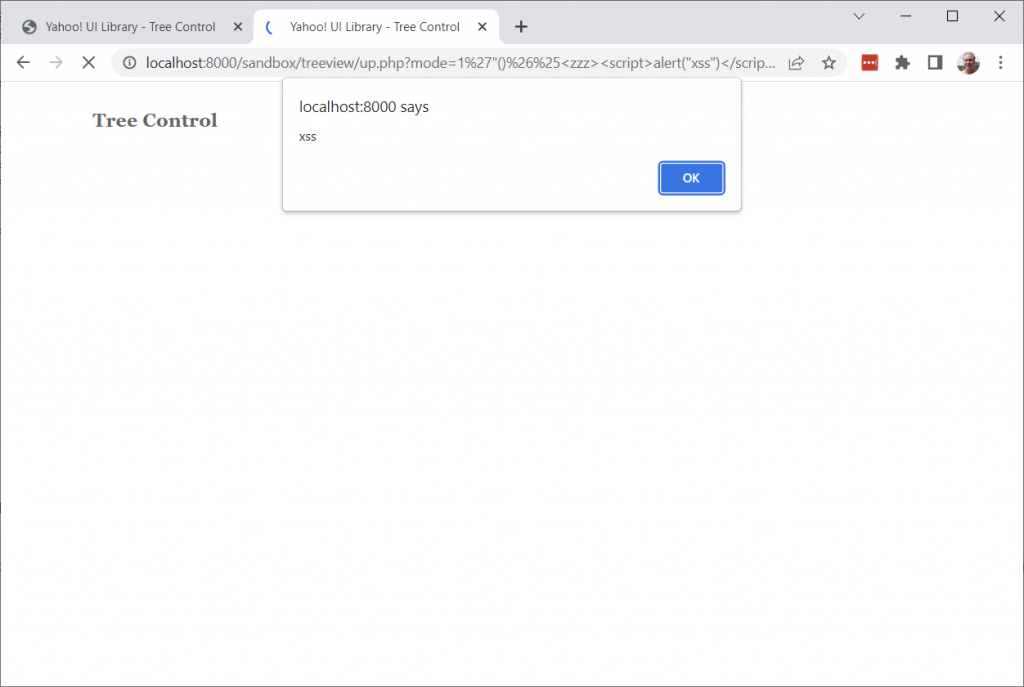
Could I reproduce the reported XSS?
Adapting the XSS links from https://github.com/ryan412/CVE-2022-48197/blob/main/README.md to my local PHP webserver, I browsed to: http://localhost:8000/sandbox/treeview/up.php?mode=1%27%22()%26%25%3Czzz%3E%3Cscript%3Ealert(%22xss%22)%3C/script%3E
Yes! Some kind of XSS can be reproduced.
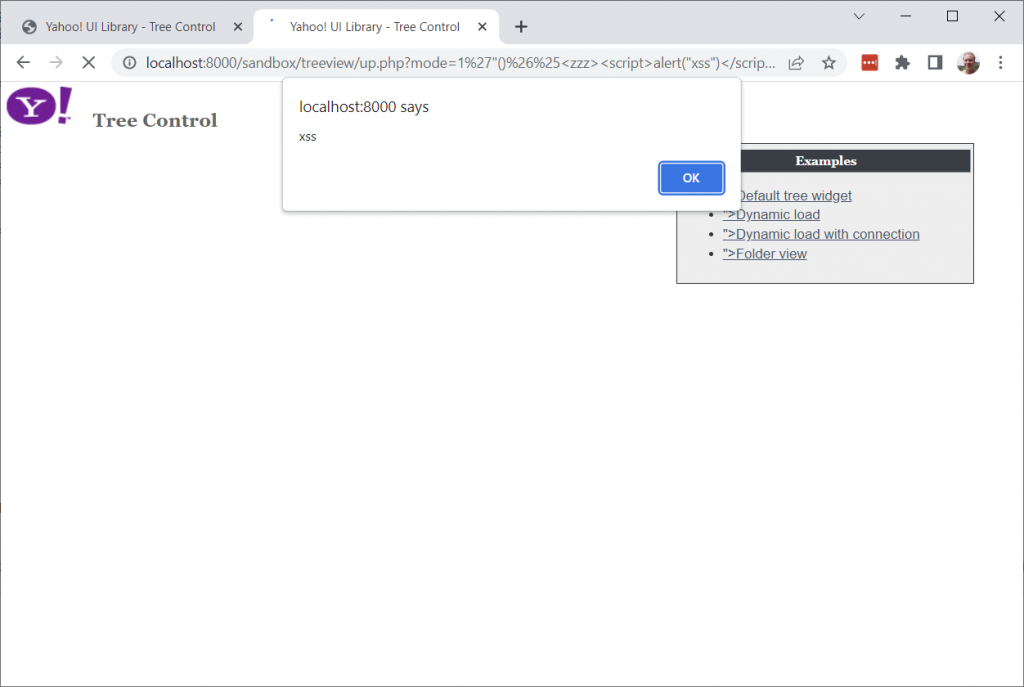
But the first clue that something in the CVE report might be fishy, was that the alert popped up repeatedly as the right-hand navigation bar renders.
Every time I accepted the alert, one more item appeared in the navigation bar! The alert was occurring while the navigation bar was rendering. Was it actually an issue with the TreeView component at all?
Where Actually is this XSS?
Looking at the reported reproducer links, they all provide a manipulated ‘mode’ parameter injecting a script element. What component is allowing the ‘mode’ parameter to leak into the page?
At the top of each PHP example (eg. ‘up.php’), are two includes — the second being ‘inc-rightbar.php’. This file implements the right-hand navigation bar to navigate between examples.
Examining ‘inc-rightbar.php’, it renders a list of links to examples; and appends the ‘mode’ parameter to each, without escaping. Here is our XSS right here!
<li><a href="default.<?php echo $ext ?>?mode=<?php echo $mode ?>">Default tree widget</a></li>
<li><a href="dynamic.<?php echo $ext ?>?mode=<?php echo $mode ?>">Dynamic load</a></li>But is this the only way in which the ‘mode’ parameter works as an attack? Could it possibly also be leaking via the TreeView component? Let’s try modifying ‘inc-rightbar.php’, and see if this removes the vulnerability.
- Replace all the
<?php echo $mode ?>statements with<?php echo "" ?>
The page can now be invoked, with no XSS.
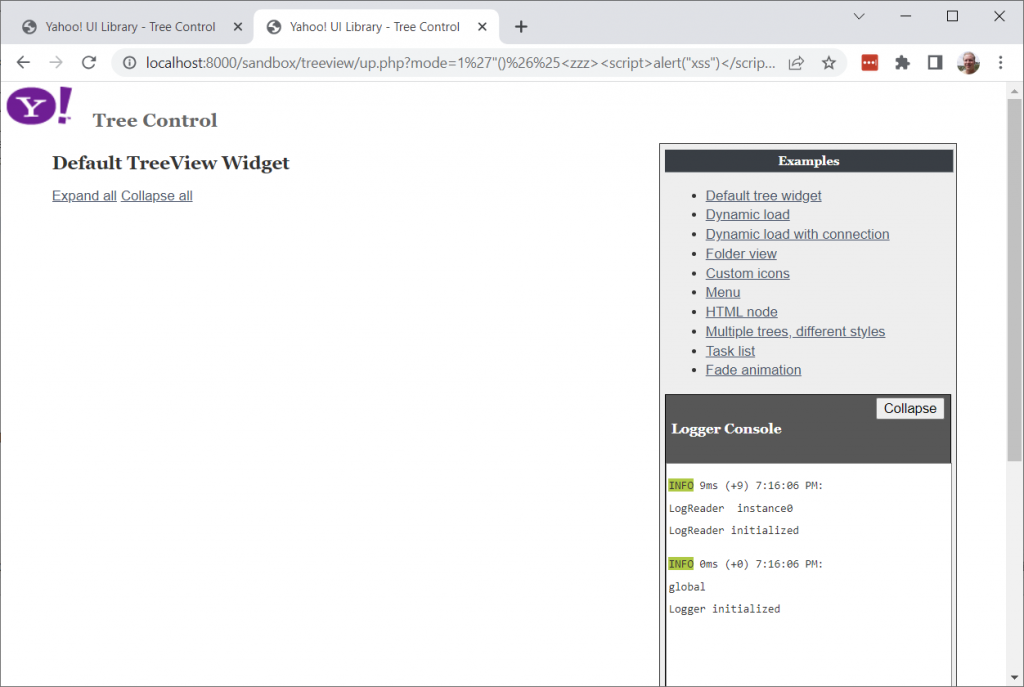
Notice that the treeview itself is no longer present. This the same as the exploit, but perhaps we should see if we can restore it just so we can be sure no vulnerability remains.
In ‘inc-alljs.php’ the ‘mode’ parameter functions as a switch selector as to whether to load minified/ build/ debug/ prod or source Javascript. In the provided repository layout ‘debug’ mode (the default) works, but ‘source’ mode (the fallback when mode is not recognized) /src/js/TreeView.js is not present.
- We will workaround for the purpose of testing by copying /build/treeview/treeview-debug.js to /src/js/TreeView.js.
Success! The TreeView now displays & functions without XSS, despite the ‘mode’ parameter being attacked.

This means that the attack is solely an attack on the Sandbar Examples Navigation — no effect via the TreeView component itself is present.
Conclusion
This reported XSS vulnerability with the YUI 2 TreeView, is not actually with the TreeView component itself; instead it is specific to a navigation panel navigating among the ‘Sandbox’ examples.
Since the Sandbox is not even included in the YUI 2 distributed artefacts (which is what I would consider the YUI 2 “product”), this would not affect users of the usual YUI library & artefacts. It seems possibly questionable whether this CVE is even correctly reportable against the YUI 2 product.
I am proposing an amended description for the CVE:
Reflected cross-site scripting (XSS) exists in Sandbox examples in the YUI2 repository. The download distributions, TreeView component and the YUI Javascript library overall are not affected.
The Sandbox examples are present in the YUI 2 repository and are described as containing examples, work in progress & experimental code. The standard downloadable distribution does not include the ‘sandbox’ directory, and is not affected. The reported XSS exists only in the ‘sandbox/treeview/inc-rightbar.php’ file providing navigation among the Sandbox examples.
Summary: This vulnerability does not affect use of the YUI TreeView component or YUI Javascript library. It is a narrow micro-vulnerability relating to example PHP pages present in the repository, but not distributed with the YUI product download.
The XSS exists in sandbox examples of YUI2 through 2800, beneath path sandbox/treeview: up.php sam.php renderhidden.php removechildren.php removeall.php readd.php overflow.php newnode2.php newnode.php.
NOTE: This vulnerability only affects products that are no longer supported by the maintainer.
See Also
- https://nvd.nist.gov/vuln/detail/CVE-2022-48197
- https://github.com/ryan412/CVE-2022-48197
- https://github.com/yui/yui2/blob/yui2-2.8.2-8/sandbox/treeview/inc-rightbar.php
- https://yui.github.io/yui2/